AWS VPC AND VPC PEERING
Hi guys I'm Anirudh, I'm passionate about DevOps and currently learning to become a skilled engineer in the field. I'm excited to connect with like-minded individuals and contribute my knowledge to the community.
Today we're about to dive into the fascinating world of VPC and would like to discuss about a project to conquer the challenge of VPC peering!
1. What is VPC?
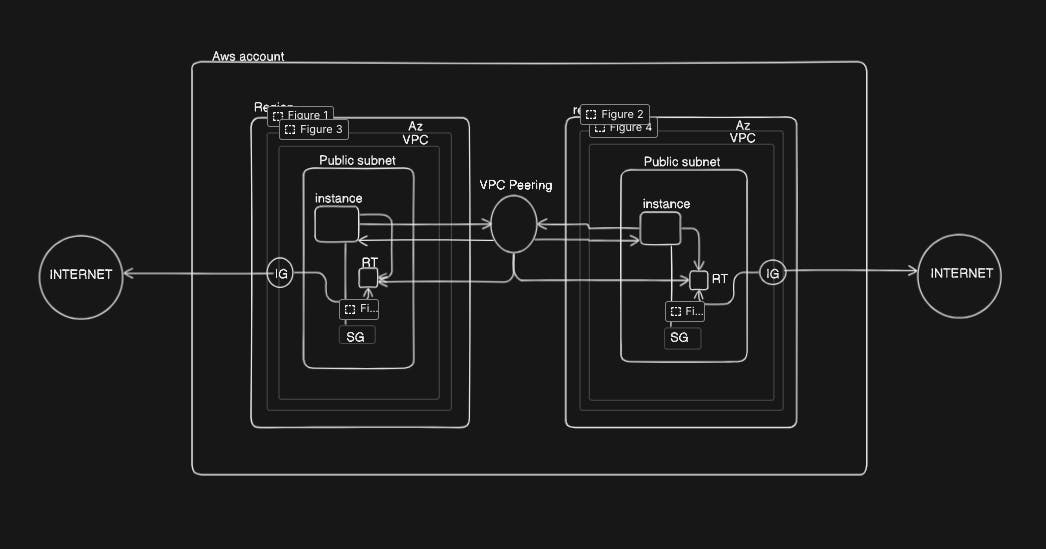
Virtual Private Cloud (VPC) - Our devices / resources runs in a network which is isolated called VPC, this means without our intervention vpc cannot get or send request from outside.
Here are few components of the VPC
Subnets: These are smaller part of your VPC that you can use to group your resources by location or function.
Route tables: These control how traffic flows within your VPC and to the outside world.
Security groups: These define the rules for inbound and outbound traffic for your resources.
Gateways: These allow your resources to connect to the internet, other VPCs, or your on-premises network.
Here are the refined points, incorporating clarity, accuracy, and additional considerations:
1. Create a VPC:
Access the VPC section of your cloud provider's console.
Initiate VPC creation, defining:
CIDR block [Classless inter domain routing]: The overall IP address range for your VPC (e.g., 10.0.0.0/16). [https://cidr.xyz/]
IPv6 CIDR block : Optional, for IPv6 support.
Name your VPC.
2. Create a subnet:
Within the VPC, navigate to subnet creation.
Specify:
Availability Zone (AZ): The physical location where the subnet resources reside.
CIDR block: A portion of the VPC's CIDR block for this subnet (e.g., 10.0.1.0/24).
3. Select availability zone:
During instance launch, choose the desired Availability Zones (Az) for placement.
Align AZ with subnet choice, as instances reside within subnets in specific AZs.
4. Launch a new instance:
Initiate instance creation process.
Select:
Instance type: Desired virtual hardware configuration (CPU, memory, storage).
AMI (Amazon Machine Image): Basically this is nothing but Operating system / software template.
VPC and subnet: The VPC and subnet created in steps 1 and 2.
Security group: Inbound and outbound traffic rules for the instance.[i suggest to let it be default]
Launch the instance.
5. Attempt SSH connection (expected failure):
Use a terminal or SSH client to connect to the instance's public IP or DNS name.
Connection failure is expected as the instance is in a private subnet without a public IP or external connectivity.
Additional considerations:
To enable SSH access, consider:
VPN: Establishing a virtual private network connection for secure access.
NAT gateway: For outbound internet access from private instances.
Review security group rules to ensure SSH access is allowed from your IP address or network.
6. Attach an internet gateway to the VPC (not subnet):
Navigate to the Internet Gateways section in your cloud provider's console.
Create a new Internet Gateway (IGW).
Attach the IGW to your VPC, not directly to a subnet. This enables internet access for the entire VPC, but individual subnets can still be private or public.
7. Create public route table:
Within the VPC, create a new route table.
Add a route with a destination of 0.0.0.0/0 (traffic from everywhere) and target the IGW.
This route table will direct all outbound traffic from associated subnets to the internet.
8. Associate public route table with subnet:
Select the subnet you want to make public.
Edit its route table association and choose the public route table you created.
This ensures traffic from instances in this subnet will flow to the IGW for internet access.
Key points:
Route tables control traffic flow within a VPC.
Public route tables direct traffic to the IGW for internet access.
Private subnets can still exist within a VPC with an IGW, using private route tables without internet access.
Additional considerations:
You should make sure that security group rules that you set will allow inbound SSH traffic for successful connections.
It is better to use EIP (Elastic IPs) for static public IP addresses for instances.
Monitor and manage internet traffic for security and cost optimization.